Guide
The Ultimate Guide to Compliance Operations

In practical terms, Compliance Operations is how organizations achieve operational compliance – making sure security and regulatory requirements are built into day-to-day workflows, not treated as one-off projects before an audit. Instead of scrambling once a year, operational compliance keeps controls, evidence, and risk management activities running continuously in the background of normal business operations. This guide walks through the fundamentals of modern compliance ops — from breaking down risk silos to automating evidence collection — so your team can embed security and regulatory requirements into everyday workflows instead of scrambling before every audit.
What is compliance operations?
Compliance Operations is an operating model and a methodology that focuses on managing information security and compliance. It helps ensure compliance and security assurance programs are managed consistently for effective IT risk management and a sustained state of operational compliance. It operates on the understanding that cyber risks can change by the minute, regulatory volatility isn’t going away, and zero trust is now the default security (and B2B purchase) model.
As such, compliance and security assurance professionals need to apply more rigor and discipline to their day-to-day activities and focus on continuous improvement. The Compliance Operations methodology provides a way for organizations to manage IT risks in a more disciplined, proactive manner and efficiently prove to their customers that they can keep sensitive customer data safe.
Key principles of compliance operations include:
Additional Resources
The majority of companies today still take a reactive approach to IT risks
According to our 2024 IT Benchmark Survey (completed by over 1,000 IT security assurance/compliance professionals),
15% of tech companies are still managing IT risks in an ad-hoc manner, with 19% managing IT risk in siloed departments, processes, and tools. While this is an improvement from the 2021 IT Benchmark Survey with 65% of global tech companies still managing IT risks in an ad-hoc way, there is still work to be done. Close to 40% of surveyed IT security assurance professionals are still manually monitoring the efficacy of security controls designed to mitigate IT risks.
65%
global tech companies are still managing IT risks in an ad-hoc way
Because organizations have a siloed approach to their risk management process, collecting critical risk and compliance information is both tedious and difficult. As such, organizations often have a limited understanding of how well existing risks are managed and limited capacity to detect when a control meant to mitigate a certain risk has failed or hasn’t been implemented effectively. All of this ultimately results in unwanted risk exposure: 59% of all survey respondents said they have experienced a data breach or privacy violation in the last two years, down only 2% from 2021.
59%
have experienced a data breach or privacy violation in the last three years
Why it’s time to evolve your approach to security assurance
The business landscape today is incredibly risk-volatile. Take a moment to consider some of the key shifts within the business landscape in the past few years and the risks these changes have introduced into organizations:
Further, the trend towards BYOD and the adoption of mass remote work due to COVID-19 has led to a widening of attack surfaces for cybercriminals. In 2020, we saw cyber attackers refine their methods to take advantage of the COVID-19 pandemic and the adoption of new technologies due to COVID-19. Online crimes reported to the FBI’s Internet Crime Complaint Center (IC3) have nearly quadrupled since the beginning of the COVID-19 pandemic.
After making the shift to mass remote work in 2020, many organizations became highly sensitized to the security and privacy risks posed by remote-work supportive technologies (e.g., teleconferencing systems). Companies have realized that when SaaS providers don’t have solid security controls within and around their systems, attackers can penetrate the SaaS providers’ IT systems and then use the vendor to launch an attack against them.
As more organizations are gaining a deeper understanding of technology risks posed by their vendors, they’ve shifted from a “trust and verify” model to a zero trust model when dealing with IT vendors.
In this context, “zero trust” means viewing third-party software vendors and business service providers as potential attack vectors — and only trusting a third party with your organization’s sensitive information after qualified auditors have had the opportunity to audit the third party’s security controls and verify their security and compliance posture.
One recent example of this shift to a zero trust approach to B2B relationships comes from the Department of Defense. Over the course of a few years, the loss and theft of government data became increasingly costly. In the fall of 2020, the DOD rolled out a new cybersecurity requirement for all DOD contractors and suppliers called the Cybersecurity Maturity Model Certification (CMMC). Instead of accepting companies’ self-assessment on security questions as valid, the DOD will only conduct business with contractors who have passed third-party audits for the appropriate CMMC level going forward.
At this time, every information business should assume that prospective customers view their business as potentially dangerous until proven otherwise. Meanwhile, there’s the simple truth that as a business adopts new technology in their quest to innovate, and more work gets done over the internet, the risk of data exposure will continue to grow.
The consequences of poor risk management practices have risen quickly. It’s not just about the monetary penalty for a compliance failure. There are a variety of costs including:
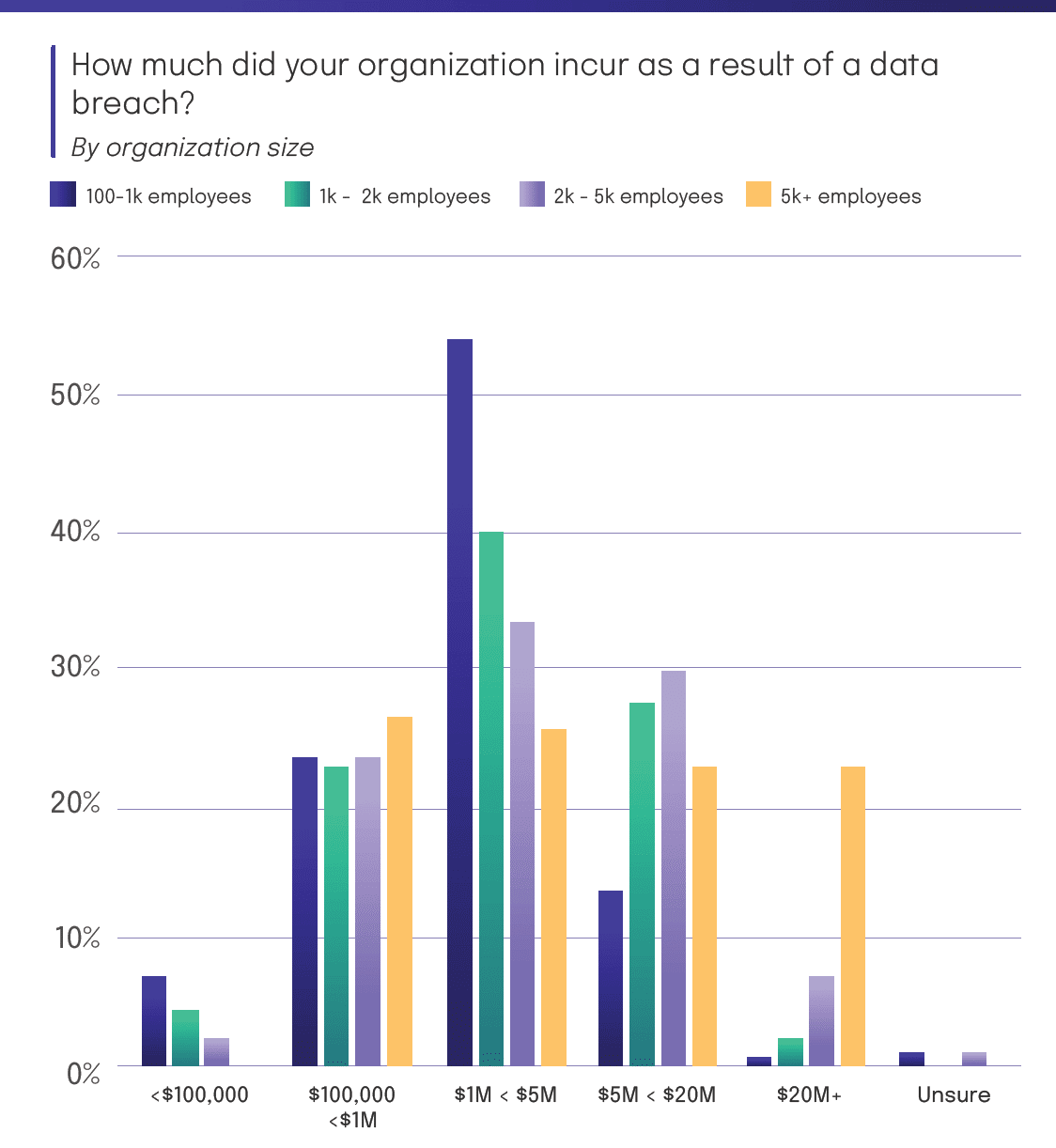
According to Hyperproof’s 2024 IT Benchmark Survey 43% of organizations who experienced a data breach in the last two years reported losing between $1M to less than $5M as a result. This is an increase of 10% compared to 2023. Notably, for the last three years, respondents reported losing $1M to less than $5M more than any other amount.
With these factors in mind, organizations today need to get better at operationalizing their security assurance and compliance activities. This involves three parts: First, implementing an internal control system designed around your organization’s specific risks is a necessity for any organization. Organizations also need to ensure that their control system — policies, procedures, and protocols — is functioning effectively, as intended, everyday. Last but not least, they need to ensure that controls are kept up-to-date as their environment changes and as external events change their risk profile. To achieve these ends, security assurance and compliance teams need better insights into their current set of risks and security posture — and modern tools that empower them to be efficient, agile, and collaborative.
Get your copy of the Compliance Operations Playbook
What are the key compliance operations principles?
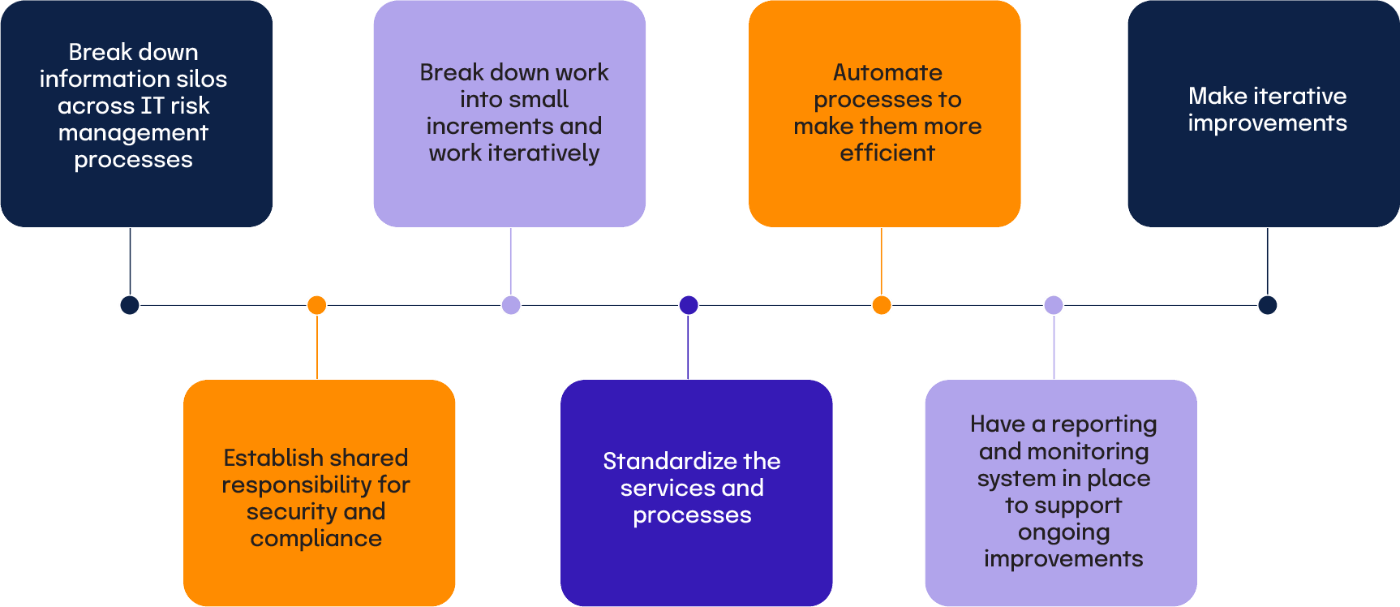
1. Break down information silos across IT risk management processes
Like any well-run business function, the security assurance/IT compliance function needs to accurately assess how they’re doing today, where improvements are needed, and what work ought to be prioritized to make the greatest impact on the business. Unfortunately, most organizations today are struggling to get a complete understanding of how well their existing risks are being managed, because they use disparate tools for different parts of the IT risk management process and information is spread all over the place. Connecting disparate information silos — so risks, security requirements and the state of the existing internal controls are well understood — is a critical step to take if an organization wants to manage IT risks in an agile, responsive way. This mapping work can be done iteratively rather than all at once.

This mapping process may seem simple, but it can’t be implemented effectively unless you have a platform that houses all of your risk information, controls, and compliance artifacts. While GRC software is intended to help with this mapping process, the ease and speed in which these exercises can be done really matters. For instance, you want a tool that allows you to collect a single set of evidence and link it to multiple controls at once. The ability to easily upload evidence in bulk and label things properly will add up to hundreds of hours saved through the course of a year.
2. Establish shared responsibility for security and compliance
If an organization wants to be consistent at mitigating risks, their information security compliance teams and business stakeholders need to share responsibility for maintaining security and compliance. This is a departure from what we see today, where many business process owners/stakeholders view compliance as something that happens off to the side.
Business process owners from HR, Finance, Engineering, and IT are operating IT systems and processes that can affect data security, integrity, and privacy. These business stakeholders and operators purchase new technology in order to improve their own productivity and to deliver better customer experiences. When new technology is purchased or when a new business process is created, new risks to information may be introduced. It’s important for the infosec compliance team to understand their business, why these business processes exist, what tools are used in these business processes, and why things are done a certain way — so they can understand the security and compliance implications.
Compliance and business stakeholders (and product engineers) should work together to ensure that IT systems are configured and used in ways that advance business objectives and adhere to internal security and regulatory standards. It’s important that the compliance team knows when business process and technology changes happen. The compliance team should document what the “proper” processes are so that what’s happening can be reviewed against the established standard. They should make this data available to the business process owners. The business process owner is accountable to ensure that the right processes or procedures are followed as they are operating their systems through the course of normal business.
This shared responsibility model can be enforced if a company is able to document all of their controls (i.e., business processes designed to mitigate a risk/ensure compliance with a regulatory requirement) and store evidence of activities around those controls in a single repository. Compliance teams should be able to see when a control process deviates from what’s deemed acceptable and have a conversation with the business stakeholder to address the issue.
3. Break down work into small increments and work iteratively

Compliance work can feel really intimidating if you think about everything that needs to be done all at once. But if you take a pragmatic and incremental approach, the work becomes much more manageable. A pragmatic approach is one that starts with your organization’s business needs in mind. For instance, what are the most critical risks within your business that need to be mitigated? Which risks need better mitigation controls? What’s the next audit that’s coming up? Is there a new security regulation or standard your business has to become compliant with in the coming months?
Knowing your current state and your business priorities, you can start to set realistic, achievable milestones and identify the most important set of tasks that need to be completed in the near term.
If you take a disciplined approach to finding out what is the current state and set incremental goals in service of improving your security and compliance posture over time, it becomes much easier to figure out the workloads and resources required to meet your objectives and allocate tasks to individuals within, and outside of, the security and compliance function.
Rather than reacting to the demands from other stakeholders, you choose to look ahead and figure out who needs to do what, and by when. For instance, what’s the cadence for internal and external audit activities? When do controls need to be implemented, reviewed, and tested? Who’s responsible for critical tasks and how do we monitor that? And finally, how can we quickly see if there’s a potential issue, like a control not being tested on schedule or if we failed to remediate a key finding?
4. Standardize the services and processes
We’ve come to expect well-defined services and processes across all areas of the organization, and in recent years even IT has adopted that mindset, using ITIL and Agile for example. Standing up well-defined services in security assurance and compliance is the logical next step, defining clear processes, roles and responsibilities and enabling a metrics-driven view of these key functions. Standardization is what turns scattered, one-off compliance tasks into a disciplined way of controlling compliance across teams – so you can see who is doing what, when, and how it impacts your overall risk posture. In the compliance realm, getting work done consistently and on-time is critical.
Start by defining a process for collecting and reviewing evidence.
If you don’t have access to up-to-date evidence, you can’t assess whether controls you’ve implemented are functioning properly or not, which may leave a key IT system exposed. Additionally, in order to pass an independent audit, you’ll need to supply your auditors with the correct compliance artifacts. Lastly, collecting evidence tends to be so tedious and time-consuming that it holds security assurance professionals back from tackling more strategic tasks. Hyperproof’s 2024 IT Compliance Benchmark Survey found that a third of the IT security compliance professionals surveyed spend 30% or more of their total time at work on repetitive administrative tasks around preparing for audits.
By having a clearly defined process for collecting and reviewing evidence and a tool that supports a streamlined process, you can save a significant amount of time, money, and frustration and minimize the risk of control failures.
When defining your evidence collection process, it’s important to consider the following:
By keeping all this contextual information alongside each piece of evidence in a system of record, you can easily reference this information for future audits — saving time and money.
5. Automate processes to make them more efficient (and support a more efficient operating environment for the entire organization)
When security compliance teams spend much of their time on manual repetitive tasks, they’re left with little time to focus on other important tasks aimed at improving security and resiliency (e.g., testing controls on high risk areas, talking to business units to understand what’s changing in the business and how those changes may create new risks or amplify existing risks). Manual, repetitive tasks, such as evidence collection, controls testing, controls monitoring, and reporting, should be automated.
Further, at the controls level, it’s easy to become “over-controlled” as compliance professionals try to meet different but somewhat similar framework requirements. This issue has driven the move towards unified controls frameworks. Automation and good processes can help us get there and remain there in light of new or changing requirements.
6. Have a reporting and monitoring system in place to support ongoing improvements

Security assurance/IT compliance work is an iterative process. Controls can quickly become obsolete when a change occurs in an organization, such as when an existing IT system is retired and a new one is implemented. To achieve continuous compliance, every organization needs to have a reporting and monitoring system that provides real-time insights into the status of internal controls, risks, audits, and automatic flagging of issues that need attention. For instance, one report should help you identify which controls need review because evidence isn’t fresh anymore. You should have an easy way to see which security objectives aren’t met yet because controls haven’t been implemented or tested. There should be a way to track issues and tasks so that those involved in compliance know what they need to do next.
7. Make iterative improvements
Infosec compliance work is never done. As your organization grows, you’ll face new compliance requirements and new risks that need to be mitigated. It’s important to look at your compliance program as a living entity and make incremental improvements on a continuous basis.
Advantages of taking an operational approach to compliance activities
The advantages of using this new operational approach – shifting from last-minute audit prep to true operational compliance – are three-fold:
Get your copy of the Compliance Operations Playbook
The key capabilities of a compliance operations platform

While it might be possible to bring discipline and rigor to these processes using the same tools we use now, it will be close to impossible to keep it that way. This is intuitive when you look at how various business functions are operating today. Sales teams have Salesforce. HR has Workday. Engineering has a variety of DevOp tools to efficiently execute their work. It’s time security assurance and compliance teams got their own platform for managing daily compliance operations – a place for making project plans, getting work done, tracking progress, and identifying areas for improvement, while controlling compliance activities in a consistent, auditable way.
Hyperproof’s compliance operations platform was built with these key principles of good operations in mind. Hyperproof is your assistant in creating a highly effective Compliance Operations function; it improves the way you plan information security, data privacy, and compliance projects, execute them and monitor progress and keep records. To go deeper into the foundational compliance capabilities every organization should develop, you can review our guide to the 10 key elements of an effective compliance program.
1. Record-keeping
Hyperproof serves as the single source of truth for all of your risks and compliance activities. Hyperproof can be where you house all infosec compliance requirements and standard frameworks (e.g. SOC 2®, ISO 27001, PCI DSS, etc.), controls universe and evidence. Evidence retrieval is easy with Hyperproof, and your organization will be well-prepared for a spot audit at any time. If you choose, you can also use Hyperproof to keep track of your risks. Risks can be mapped back to existing controls — allowing you to understand how well existing risks are managed.
2. Planning
You can use Hyperproof to determine your scope of work and what needs to be done to meet compliance frameworks’ requirements (e.g., what controls need to be created), identify owners and contributors to the work, create timelines, and assign tasks. Equally important, Hyperproof will help you identify existing controls you can leverage to meet requirements for new compliance frameworks.
3. Workflow optimization and automation
Cut the time your team spends on manual tasks by up to 70 percent, and free up time to work on the most impactful activities. With Hyperproof, you can improve productivity by automating manual tasks (e.g., collect evidence automatically, set automated reminders for others to submit evidence) and remove friction points from collaborative processes.
4. Reporting and monitoring
Hyperproof makes it easy for everyone within your organization to get on the same page about what the current state of your compliance efforts are and where improvements are needed. With real time analytics, your team knows exactly where they should spend their time and energy. Potential problems, such as out-dated controls, are identified early before they metastasize into costly incidents.
5. Scaling
Hyperproof helps organizations easily scale up their information security compliance programs and manage multiple audits. With Hyperproof, you can map a control to multiple frameworks’ requirements and re-use evidence across multiple audits. For teams coordinating requirements across regions and business units, compliance software for multinational operations like Hyperproof makes it easier to apply a consistent control framework while still meeting local regulatory nuances.
By combining the compliance operations key principles with the Hyperproof compliance operations software, you’ll bring rigor, consistency and efficiency to your security assurance and compliance program.
Get your copy of the Compliance Operations Playbook
How to implement compliance operations principles with Hyperproof
Now, here’s how you can operationalize these compliance operations principles step by step with Hyperproof. Each of the five steps builds on top of the previous one.
Step One
Get everything into a single place
Breaking down information silos so that risks and the state of the existing internal controls are well understood has to be the first step if an organization wants to manage IT risks in an agile, proactive way. Hyperproof serves as the single source of truth for all of your risks and compliance activities, including documentation of controls, evidence (or compliance artifacts), and records of audits.
Typically, organizations start using Hyperproof by populating an existing template.
Out of the box, Hyperproof provides a set of illustrative controls for many of the most commonly used security and privacy frameworks, including NIST-CSF, PCI-DSS, ISO 27001 and many others. These starter controls are linked to program requirements (or security objectives), providing a quick start approach for many organizations. For organizations who already have existing controls in place, it’s quite simple to edit the provided controls, add new controls, and remove superfluous ones.
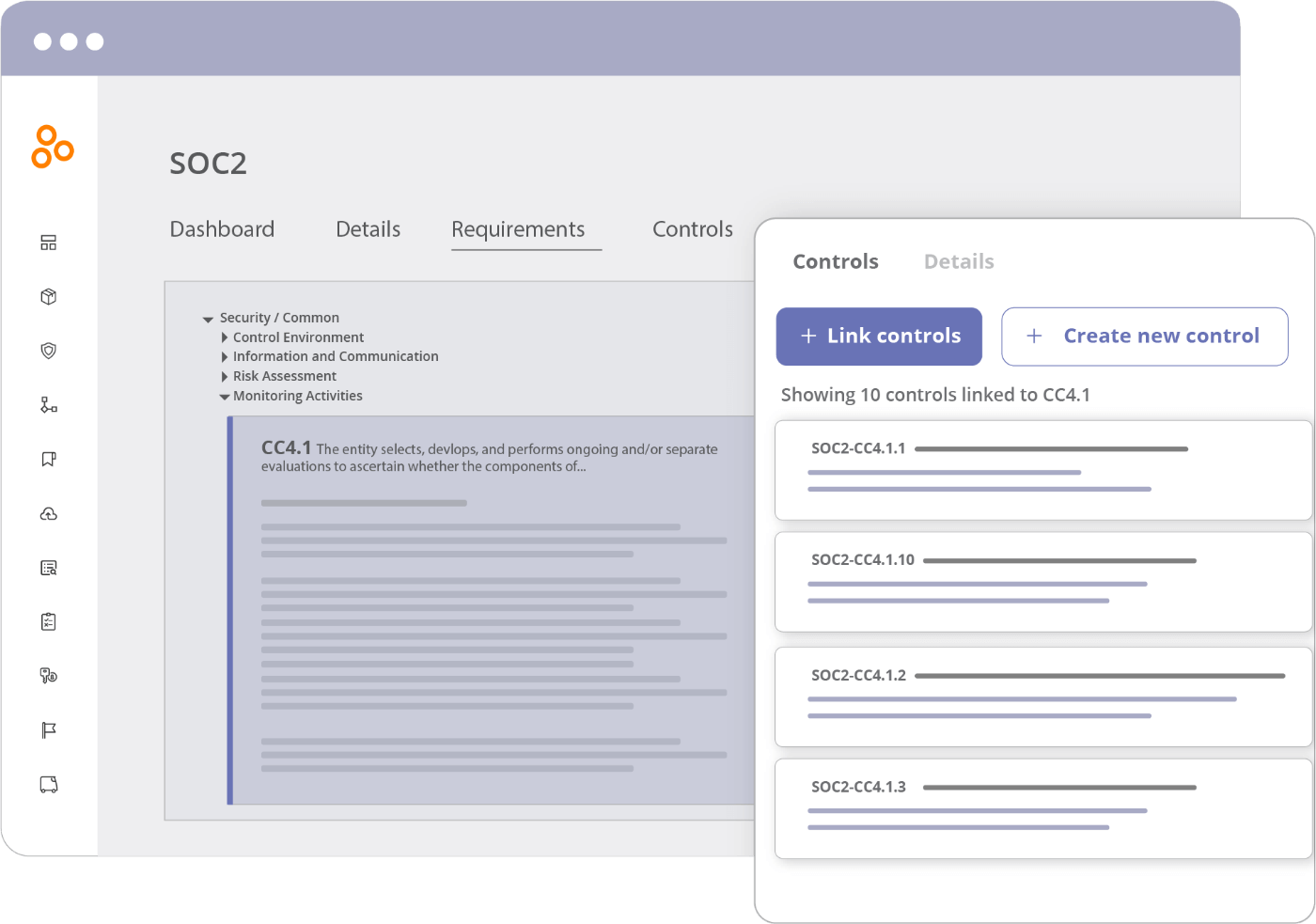
By using Hyperproof, it’s easy to keep track of what controls are already implemented and operational, versus which ones are missing – so additional work can be identified and assigned to the responsible parties.
Once you select a specific template, you can immediately start uploading your evidence into the system and link them to the controls.
You can also track your risks in Hyperproof in a risk register. Each risk can be mapped back to controls in Hyperproof — so you can understand how risks are mitigated with existing controls and your residual risk.
Step Two
Define the responsible parties and their roles and responsibilities
Hyperproof makes it easy to define clear processes, roles, and responsibilities and monitor how key functions are performing, so you’re able to avoid compliance slip-ups, control deficiencies, and failing audit results.
Assign control ownership: One of the most common causes of IT system failures and compliance lapses is that companies aren’t keeping controls up-to-date. The real problem starts upstream: When no one in the company knows who is responsible for maintaining specific controls. Hyperproof lets you assign controls to individuals or teams and re-assign a control when there’s a change in personnel. This visibility into “who is responsible for what” is essential for staying on top of your compliance obligations.
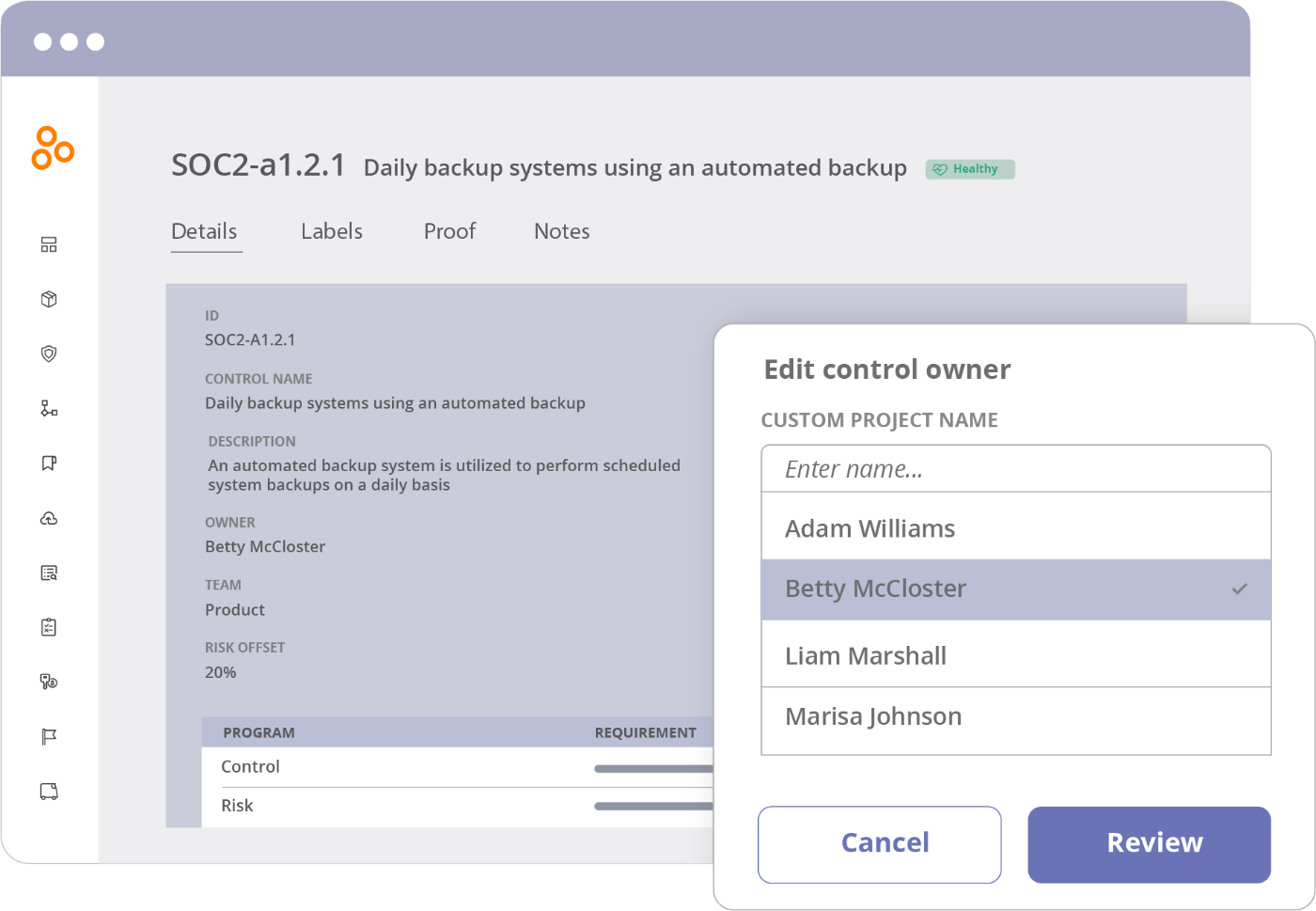
Define cadences for control monitoring: To minimize IT risks, controls need to be critically observed, monitored, and reviewed on an ongoing basis. However, this task is extremely difficult to accomplish if you don’t have the appropriate technology that automates the work. In Hyperproof, you can define cadences to review controls and set due dates. Then, the system takes over the job of reminding people to get their work done.
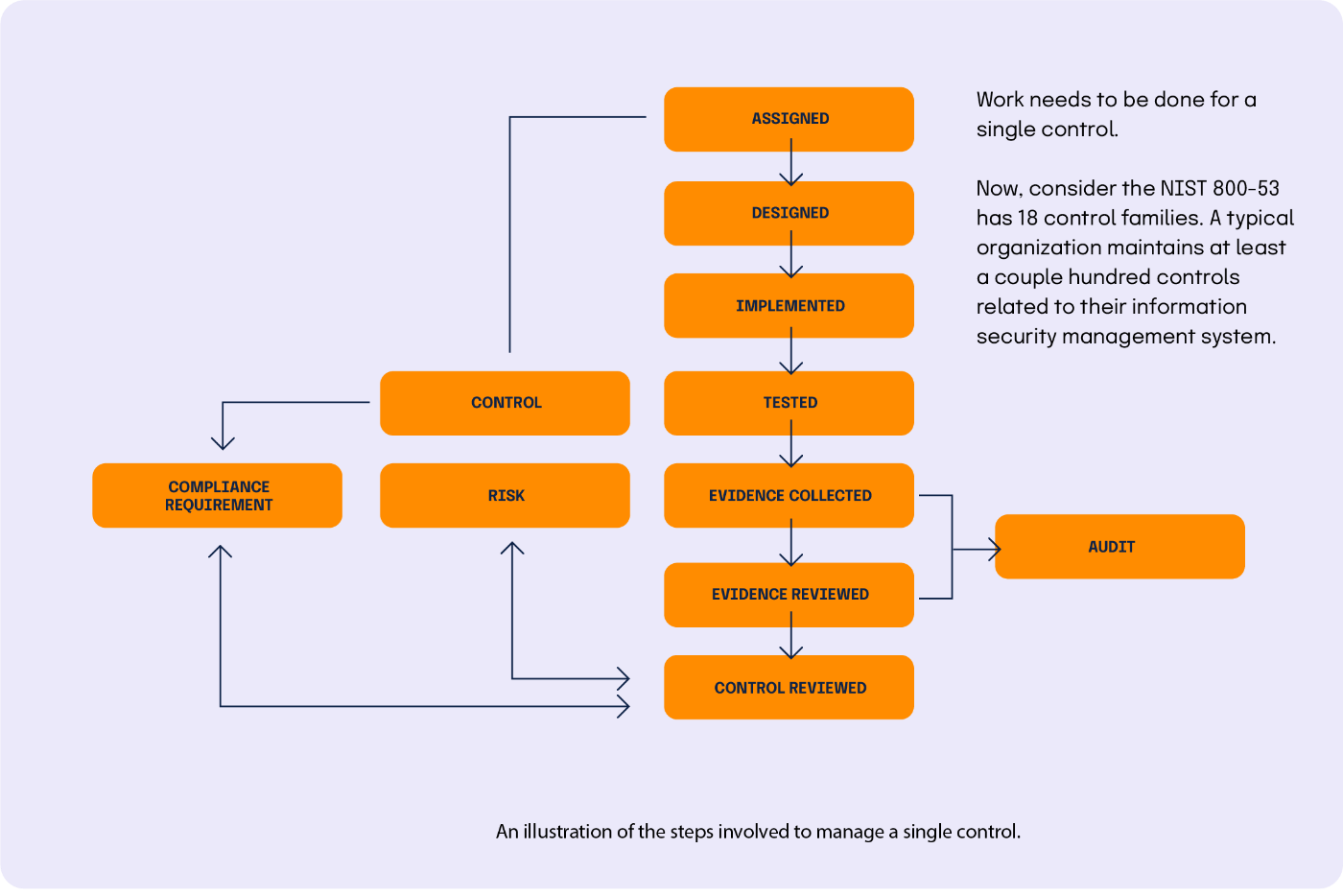
Step Three
Streamline your evidence management workflows
With Hyperproof, you can build an organized and highly efficient evidence collection and review process and ensure it stays that way. Here is how our software supports this:
Step Four
Free up time by reducing friction points from collaboration processes
In the security assurance and compliance realm, getting work done requires ongoing collaboration between those inside and outside of the security assurance and compliance functions and between those inside and outside of an organization. To operate efficiently, compliance teams need tools in which they can easily assign tasks, track the completion of those tasks, and communicate with parties involved in those tasks. It’s also important to minimize switching back and forth between multiple tools. If these conditions aren’t met, it’s all too easy for individuals to drop the ball. With Hyperproof, you can:
Step Five
Monitor, measure, and iterate to maintain continuous compliance
New IT risks can be introduced by internal operational changes or unexpected circumstances. To protect your organization, your security assurance and compliance teams need to understand how internal and external factors introduce new risks, amplify existing risks, and evolve the control environment to keep risks in check.
With Hyperproof’s dashboards and reports, you can stay on top of risks and your control environment at all times and iteratively evolve and mature your risk management and compliance management practices.
How are compliance operations platforms different from traditional GRC tools?
Although GRC tools have existed for over a decade, most have their roots in risk tracking and/or policy management. They weren’t built for the tasks today’s security assurance and compliance professionals must tackle. This category of software was born at a time when cybersecurity and data privacy regulations were a less onerous burden on information-based businesses than they are now. Fast forward to 2021: it’s not unusual for a mid-size organization to have hundreds of business applications and processes that affect the security of information. The number of stakeholders involved in security compliance has risen exponentially. As such, compliance professionals need to collect proof of security controls from many more places and people than they’ve had to in the past.
Specifically, traditional GRC tools are not meant to help organizations with collecting and managing evidence on a continuous basis — a highly tedious, yet necessary task for maintaining a solid security posture. Further, they’re often not intuitive to use and thus require a lot of training before people are comfortable on the platform.
On the other hand, compliance operations software like Hyperproof is specifically built for today, when protecting information — and your ability to prove you can protect that information — has become paramount to business success. Compliance operations software like Hyperproof’s purpose is to help security assurance and compliance professionals stay on top of critical risk management activities and manage those activities in the most efficient way. For instance, Hyperproof can help an organization effectively structure their infosec compliance program (e.g., understand similar requirements across multiple frameworks to minimize redundant work), automate evidence collection and management, reduce audit fatigue, and gain real-time visibility into control performance and update controls whenever it’s needed.
Get your copy of the Compliance Operations Playbook
Download the PDF












